I love a good crackme. It was one of the first things I practised when I did my first CTF (Pico) this year. This challenge is for newcomers to Reverse Engineering.
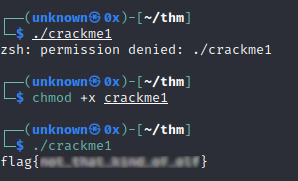
Crackme1
Nothing special, you just need to give execution permissions to the binary and then execute it.
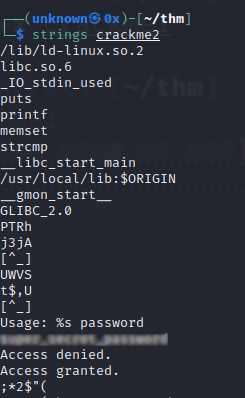
Crackme2
This binary asks us for a password and, if we get it right, it will print the flag for us. After simply running strings on the file I can clearly see the password which has been hard-coded into the check, but the flag is nowhere to be seen. So, then I execute the program and supply the password, and I receive the flag.
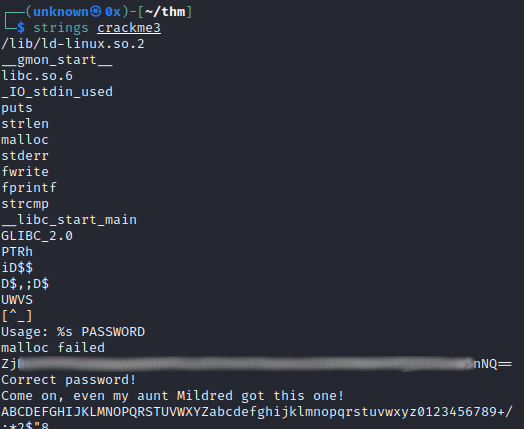
Crackme3
This one we also just run strings and see the tell-tale double equals of base64 (and also its character set, as a string), which we then decode with Cyberchef:
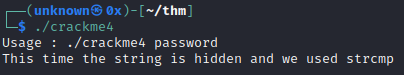
Crackme4
With this one we actually have to break out some RE tools. The binary tells us to call it with the password as an argument. The string we are searching for is hidden and it tells us the function used is strcmp.
So, we launch gdb and look at the function table:
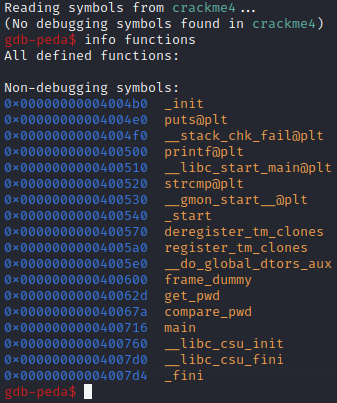
We set a breakpoint on this function so that we can look at the contents of registers when the flag has been loaded in:
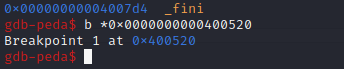
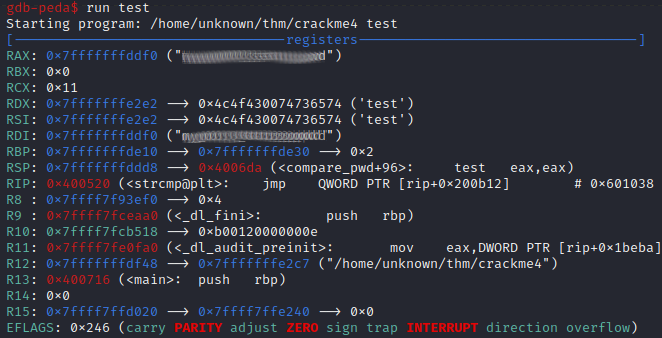
We then run the program and supply a random word as input for the password check. We can see the answer loaded into RAX/RDI.
Crackme5
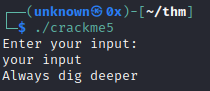
Running strings on the binary produces nothing useful, running it is pretty cryptic as every input returns “always dig deeper”.
Launching Ghidra, we find the function responsible for the main string comparison, called strcmp_:
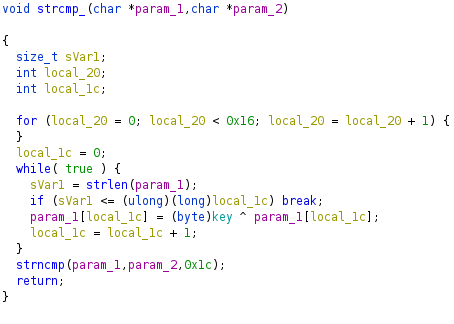
After reading it carefully we can see it creates a for loop for 22 iterations, then creates a while loop with a check on the length of the first input string vs the incrementing integer local_1c. So, for the length of the string, take the next character and XOR it with a global variable named key. Then we do the comparison.
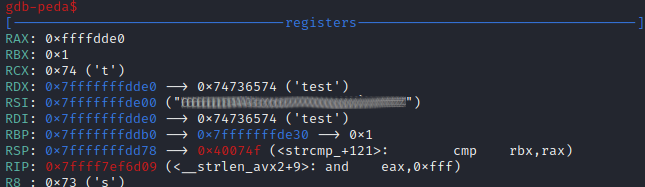
This means the answer is going to be loaded into memory when the comparison takes place, so we’ll use gdb as above, and with a breakpoint on strcmp_ we find the “answer” in RDX/RSI.
Crackme6
We get no useful information from execution:
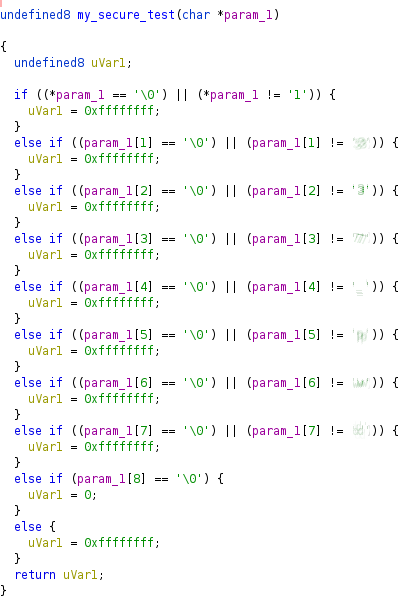
But strings finds a function called my_secure_test:
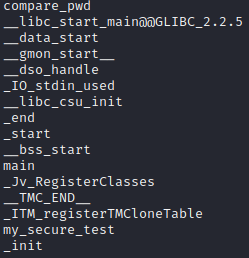
So after opening in Ghidra, we find this forgotten test function at the “top” of the binary and it’s quite telling, as it spells the password:
Crackme7
This time we get a small program which can add two numbers or say hello to the user. There does not appear to be any “challenge”, and it’s unclear if we need crafted input for the name or the numbers to add. Opening the program in Ghidra gives us the answer:
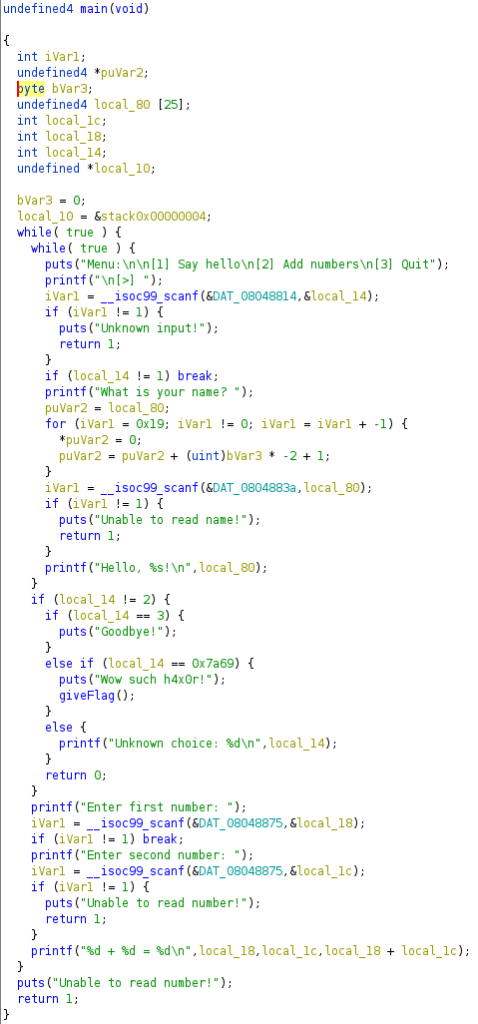
So we check if the input is 1, for a hello command, then we check if it’s equal to 2. If not, we evaluate for the exit command, and then we check if it’s equal to 0x7a69 in hex. This is the password, and when we enter it as a choice at the main menu, we get the flag.
Crackme8
Again we need to call the binary with the correct password as an argument. Strings produces nothing interesting. Ghidra shows more:
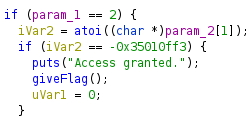
We have a secret encoded value which is checked against our input in the main function. As it is converted to a number before the check, we can enter the value in decimal form, which is suggested by Ghidra when we hover over the value.
Overall it is a good practice CTF for RE techniques but it could have gotten more challenging for the later tasks.